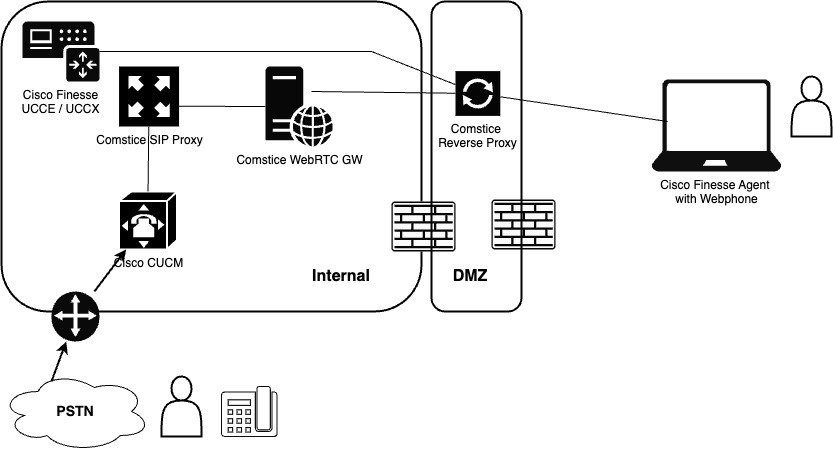
Comstice Reverse Proxy is used in many Cisco Finesse solutions such as Cisco Finesse Webphone Gadget, Cisco Finesse Agent Portal, Cisco Finesse Desktop Softphone, and Cisco Finesse Mobile Softphone. This document explains how Comstice Reverse Proxy handles any risks around DDoS and the features available.
IP Address Whitelisting
Comstice Reverse Proxy hosts the initial login page where we validate the remote users, enable SSO with MFA. It also whitelists the IP address of the successfully validated users.
Here are some features that will be implemented to help mitigate DDoS attacs.
- Rate Limiting
- Limit Connections: You can limit the number of connections from a single IP address using the limit_conn directive. This can be applied to the overall server or to specific locations.
- Limit Request Rate: The limit_req directive allows you to limit the rate of requests coming from a single IP. This can be particularly useful for throttling UDP requests or frequent TCP connections.
limit_req_zone $binary_remote_addr zone=req_zone:10m rate=5r/s; limit_req zone=req_zone burst=10 nodelay;limit_req_zone $binary_remote_addr zone=req_zone:10m rate=5r/s; limit_req zone=req_zone burst=10 nodelay; - Connection Timeout
- Client Timeout: Configuring a low client_body_timeout and client_header_timeout can help drop connections that are deliberately slow to keep the server busy (slowloris attacks).
client_body_timeout 10s; client_header_timeout 10s; - Request and Connection Limits
- Buffer Size Limits: Setting maximum buffer sizes using directives like client_body_buffer_size and client_header_buffer_size can prevent attackers from overwhelming Comstice Reverse Proxy with large requests or headers.
- Max Connections and Requests per Server: You can also limit the total number of simultaneous connections using worker_connections and worker_rlimit_nofile.
worker_connections 1024; worker_rlimit_nofile 2048; - Access Control
- Deny Access: You can use the deny directive to block specific IP addresses or ranges that are known to be malicious.
deny 192.168.1.1; deny 10.0.0.0/24; allow all; - TCP/UDP Specific Directives (Stream Module)
- Limit Connections for TCP/UDP: With the Stream module, you can limit the number of connections to TCP/UDP services.
stream { limit_conn_zone $binary_remote_addr zone=conn_zone:10m; server { listen 12345; limit_conn conn_zone 10; } } - GeoIP Blocking
- GeoIP Module: You can restrict access based on geographical locations using the GeoIP module, which can be effective in blocking traffic from regions that are not expected to access the service.
geoip_country /usr/share/GeoIP/GeoIP.dat; map $geoip_country_code $allowed_country { default no; US yes; CA yes; } server { if ($allowed_country = no) { return 403; } } - Dynamic Blocklist
- Automated IP Blocking:Use modules like Fail2Ban or integrate with dynamic blocklist providers to block IP addresses that are exhibiting suspicious behavior automatically. Fail2Ban can monitor logs and update Reverse Proxy's access control based on patterns of malicious activity.
- Caching
- Response Caching: For repetitive requests, enable caching to reduce the processing load on Comstice Reverse Proxy and the backend servers. This can help mitigate the impact of a flood of identical requests.
- SSL/TLS Rate Limiting
- SSL Handshake Limits:You can also limit the rate of SSL/TLS handshakes to protect against SSL-based DDoS attacks.
limit_conn_zone $binary_remote_addr zone=ssl_handshake_zone:10m; limit_conn ssl_handshake_zone 10; - Use of External Tools
- WAF (Web Application Firewall):Integrating Reverse Proxy with a Netscaler can provide advanced filtering and protection against Layer 7 DDoS attacks.
- Monitoring and Alerts
- Log Monitoring:Regularly monitor Reverse Proxy logs via Syslog for unusual patterns of traffic that may indicate a DDoS attack in progress. Implement alerting systems to notify administrators of suspicious activity.
Protecting Open UDP Ports from DDoS
- Rate Limiting:
- Rate Limit UDP Traffic:Implement rate limiting at the network level to control the amount of traffic that can be sent to a particular UDP port. This can be done using tools like iptables or in the network infrastructure (e.g., routers or switches).
iptables -A INPUT -p udp --dport 12345 -m limit --limit 10/s -j ACCEPT
iptables -A INPUT -p udp --dport 12345 -j DROP - IP Filtering and Whitelisting:
- IP Whitelisting:Restrict access to the UDP port to only known, trusted IP addresses. This can be implemented through firewalls or access control lists (ACLs).
- GeoIP Filtering:If your service is regional, you can use GeoIP filtering to block traffic from regions where legitimate traffic is not expected.
- Application Layer Protocol Validation:
- Deep Packet Inspection (DPI):Use DPI to inspect the content of UDP packets and ensure that they conform to expected protocols. Malformed or unexpected packets can be dropped, reducing the impact of a DDoS attack.
- Use of Reverse Proxies and Load Balancers:
- UDP Reverse Proxy:Similar to TCP, a reverse proxy can be used to distribute UDP traffic across multiple servers, reducing the impact of a DDoS attack on a single server.
- Load Balancers:Deploy load balancers that can detect and mitigate DDoS attacks by distributing traffic across multiple servers and providing rate-limiting features.
- Network-Level Filtering:
- Ingress Filtering:Implement network-level ingress filtering to block spoofed packets. This can be done using BCP38, which prevents IP address spoofing by verifying that incoming packets are from legitimate sources.
- Blackholing:In case of a large-scale attack, blackhole routing (null routing) can be used to drop all traffic to the targeted IP address temporarily.
- Protocol-Specific Protections:
- DNS Response Rate Limiting (RRL):If your service involves DNS (which uses UDP), you can implement DNS RRL to mitigate DNS amplification attacks.
- NTP, Memcached, and SNMP Protections:For services like NTP, Memcached, or SNMP that use UDP, ensure they are configured securely (e.g., disabling monlist in NTP, using authentication in SNMP) to avoid being used in amplification attacks.
- Logging and Monitoring:
- Real-Time Monitoring:Implement real-time monitoring to detect abnormal traffic patterns that might indicate a DDoS attack. Tools like NetFlow, sFlow, or custom monitoring solutions can provide insight into traffic behavior.
- Automated Response:Set up automated responses that trigger when a potential DDoS attack is detected, such as dynamically adjusting firewall rules or rate limits.
- Firewall Configuration:
- UDP Flood Protection:Configure your firewall to detect and block UDP flood attacks. Many modern firewalls come with built-in DDoS protection features that can help mitigate UDP floods.
- Honeypots and Decoys:
- Deceptive Techniques:Deploy honeypots or decoy services on non-critical UDP ports to attract and analyze attack traffic. This can help in understanding attack patterns and can also delay attackers, giving you more time to respond.
- Service-Specific Hardening
- Service Configuration:Ensure that the application or service listening on the UDP port is hardened against attacks. This might include optimizing how the service handles incoming traffic and ensuring it can gracefully handle high volumes of requests.
- Reducing Attack Surface
- Minimize Open Ports:Only expose necessary UDP ports to the public internet. If a service does not need to be accessible from all locations, restrict its exposure as much as possible.
- Anycast Networks:
- Anycast Routing:Deploy your services on an Anycast network to distribute traffic across multiple geographically dispersed nodes. This can help absorb and mitigate DDoS traffic by spreading it across a wide area.
By combining these strategies, we are able to significantly reduce the risk of successful DDoS attacks on UDP ports.
How IP Whitelisting Protects the port that is already open?
IP whitelisting is a security measure that allows only specified IP addresses to access a particular service, such as a port. While it's true that the port remains technically "open," IP whitelisting restricts which IP addresses are allowed to communicate with that port. Here’s how IP whitelisting can protect a port, even if it's open:
- Restricting Access to Trusted Sources:
- Controlled Access:With IP whitelisting, only IP addresses on the whitelist can send or receive traffic to and from the port. All other IP addresses are blocked, effectively limiting access to a small, trusted group of users or systems.
- Reduced Attack Surface:Even though the port is open, it's not accessible to the general public. This significantly reduces the attack surface since only specific, known IP addresses can interact with the service, minimizing the risk of unauthorized access.
- Blocking Unauthorized Traffic:
- Prevention of Unauthorized Access:If an attacker tries to send traffic to the port from an IP address that is not whitelisted, the firewall or access control list (ACL) will block the traffic. This prevents unauthorized or malicious traffic from reaching the service.
- Defense Against Scanning and Probing:Attackers often scan open ports to find vulnerabilities. IP whitelisting helps protect against these scans because, even if an attacker discovers that a port is open, they won't be able to interact with it unless their IP address is on the whitelist.
- Mitigating DDoS Attacks:
- Limiting the Scope of DDoS Attacks:In the case of a DDoS attack, IP whitelisting can limit the impact by allowing only legitimate traffic from whitelisted IP addresses. While it doesn't prevent the attacker from sending packets, the firewall or network devices will drop packets from non-whitelisted IPs, reducing the load on the server and mitigating the attack's effectiveness.
- Focused Security:By whitelisting IP addresses, you ensure that only traffic from trusted sources is processed by your application. This reduces the chances of your service being overwhelmed by malicious traffic, as most attack traffic will be discarded by the network perimeter before reaching the application.
- Operational Simplicity:
- Simple Configuration:IP whitelisting is straightforward to configure on most firewalls or networking devices. It provides a clear and manageable way to control access, especially when only a limited number of clients or locations need access to the service.
- Less Resource Intensive:Because IP whitelisting is typically implemented at the network level, it prevents unwanted traffic from even reaching the application layer, conserving server and application resources.
- Granular Control:
- Per-Port Whitelisting:IP whitelisting can be applied to specific ports, meaning you can restrict access to sensitive services (like administrative interfaces) while leaving other, less sensitive ports accessible to a broader range of IPs.
- Layered Security:Whitelisting can be part of a layered security approach, where it's combined with other measures like rate limiting, deep packet inspection, and anomaly detection to provide comprehensive protection.
Example Scenario
Imagine you have a UDP-based service running on port 12345. If the port is open without any IP restrictions:
- Without Whitelisting:Anyone on the internet can send packets to this port. An attacker could flood it with traffic, potentially causing service disruption.
- With Whitelisting:You configure your firewall to only allow traffic from a specific IP range (e.g., 192.168.1.0/24). Now, if an attacker tries to flood the port from an IP outside this range, the firewall blocks the traffic, preventing the attack from reaching the service.
Summary
While IP whitelisting doesn't close the port in the sense of making it completely inaccessible, it does enforce strict controls over who can access the service on that port. This significantly enhances security by ensuring that only trusted, pre-approved sources can interact with the service, thereby protecting it from unauthorized access and various forms of attack.

